This post will explain how to setup your computer in order to dual boot Backtrack 5 and Windows. The difficulty is to have both operating systems fully encrypted. This guide will be focused on Backtrack 5 (Gnome desktop) and Windows 7. It should be straightforward to follow this guide using a different version of Windows. If you want to install a different Linux distribution the instructions can differ significantly.
Truecrypt will be used to encrypt the Windows installation and dm-crypt using LUKS to encrypt Backtrack. The requirements to follow this guide are having the Windows and Backtrack installation CD ready to use.
To clarify an important point: I use full disk encryption to protect my data in the event my laptop may be lost or stolen. It will not protect you in case an adversary forces you to reveal your password. For such situtions you can use
deniable encryption which is also
provided by truecrypt.
Preparation
Format
Before we begin the installation we will perform an anti-forensic format of the complete hard drive. This is a fancy way of saying that we will use a tool to overwrite the complete hard disk with random data. It's needed because simply deleting all your files won't actually delete them. Instead they will be simply marked as deleted and may be overwritten with new data in the future. So an attacker might still be able to retrieve your supposedly deleted files.
Another problem is that it might be possible to retrieve your old data even if it has been overwritten with new data. This can for example be done with a technique such as
magnetic force microscopy. To defend against these kinds of attacks we will overwrite the complete hard drive data several times with random data.
Because securely formatting the hard drive was not my main goal I personally used the tool shred. It's available in the backtrack live CD and can be started with "shred /dev/sda". Another tool you can use is
DBAN, which is a live CD allowing you to securely wipe an entire hard disk.
Partitioning
Because the partition manager that is available during the installation of Backtrack is limited in functionality we will use gparted to partition the hard disk. So start the Backtrack live CD, open a terminal and type "apt-get install gparted" to install it. Then start it be executing "gparted".
Click on Device -> Create Partition Table. The default is to create an MS DOS partition and this is what we need, so click on Apply. Now we can create the partitions. At minimum you will need the following partitions:
- One partition that will contain Windows. During the installation we will first use this space to install an unencrypted Backtrack system. Afterwards we will install Windows on it. Hence this partition must first be formatted as an ext4 partition and in the future we will format it to NTFS for windows.
- One ext4 partition that will contain the (unencrypted) files necessary to boot the encrypted backtrack installation. Hence a 370 MB ext4 partition will suffice.
- Preferably, but not strictly necessary, one Linux swap partition. The ideal size depends on how much RAM you have. Since I have 4 GB ram around 800 MB swap space should suffice.
- One ext4 partition that will contain the encrypted Backtrack installation. For this I have chosen for a 20 GB ext4 partition.
As mentioned we will first install Backtrack on the partition that will eventually contain Windows. This is done because we can't directly install Backtrack on an encrypted partition. Therefore we will first install it to an unencrypted partition and then copy all the files to the encrypted partition. Once that is done we will format the Windows partition to NTFS and install Windows on it.
Depending on the size of your hard disk and preferences you can customize the number and sizes of the partitions. Anyway, I will now detail how to create these basics partitions. First select the unallocated space and click on Partition -> New. Fill in the options as shown below (the partitions sizes may differ for you).
Create an extended partition for the remaining unallocated space. Now continue by creating the other partitions to your liking. I ended up with the following table which you can also use if you want (again, sizes may differ).
Click on Edit -> Apply All Operations to write the changes to disk. Close gparted. In the remaining of this guide I will use the device names as shown in the previous image. That is, the device names correspond to the partitions as follows:
- /dev/sda1: Windows partition (temporarily used to first install Backtrack)
- /dev/sda5: Unencrypted boot partition
- /dev/sda6: Swap partition for Backtrack
- /dev/sda7: Encrypted Backtrack partition
If you use a different partition scheme be sure the use the correct device names in the commands listed throughout this guide.
Installing Backtrack 5
Start the graphical installer of Backtrack 5 and fill in the correct information until you get to "Prepare disk space" where you must select "Specify partitions manually (advanced)".
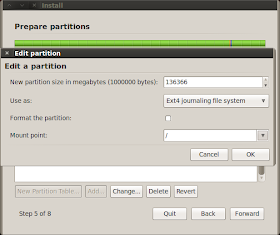
In the next step click on /dev/sda1 and then on "Change" and select it to be an ext4 partition that mounts to /. Do not change the partition size!
Now do the same for /dev/sda5, so set it to ext4 but this time mount /boot. I have ended up with the following configuration:
When clicking on "Forward" it might tell you that some file systems are not marked for formatting but the files on it will nevertheless be deleted. Simply click on continue and proceed with the installation.
Once the installation has finished you can restart your computer to ensure everything is properly installed.
Downgrading to GRUB
At the time of writing this guide GRUB 2 is unable to chainload the truecrypt bootloader (at least to my knowledge and without annoying workarounds). For this reason we will downgrade to GRUB (grub legacy) which will be able to handle everything perfectly and offers the same functionality.
Start the Backtrack system you have just installed and open a terminal. To remove GRUB 2 execute "apt-get purge grub-pc". If it asks to remove all GRUB 2 files from /boot/grub select yes. Then execute "rm /boot/grub/core.img" to get rid of the remaining GRUB 2 files. Your computer won't be bootable until we install the old version of grub.
Install grub by executing "apt-get install grub". Configure grub to load during boot by executing "grub-install /dev/sda". Finally configure the grub boot menu by executing "update-grub". It should say "could not find /boot/grub/menu.lst ...". Enter yes to create the menu. Reboot the system to verify it boots properly.
Note: The grub menu will now display "Ubuntu 10.04.2 LTS" instead of Backtrack 5. At the end of this guide we will clean up this menu entry.
Encrypting Backtrack
Encrypted Partition
From your backtrack installation open a terminal. To be sure we have all the packages we need execute the command "apt-get install cryptsetup hashalot initramfs-tools". For Backtrack 5 only hashalot will be installed, as cryptsetup and initramfs-tools are already included in the default installation.
We have to create an initial ramdisk (initrd/initram) that contains all the necessary tools to boot a basic linux environment that will ask for your password and is able to decrypt the encrypted Backtrack partition during boot. An initial RAM disk is an initial root file system that is mounted prior to when the real root file system is available (which is in our case encrypted). We will create it using initramfs-tools.
To specify that the partition needs to be decrypted during boot execute the following single command:
echo "CRYPTOPTS=target=cryptroot,source=/dev/sda7" > /etc/initramfs-tools/conf.d/cryptroot
This will create the file /etc/initramfs-tools/conf.d/cryptroot with the given line as its content. Execute "update-initramfs -u" to apply these changes. Now run the following commands to create an encrypted partition:
- modprobe dm_crypt
- modprobe sha256_generic
- luksformat -t etx4 /dev/sda7
For the last command be sure to type an uppercase YES. Otherwise it will give the cryptic error message "Cloud not create LUKS device /dev/sda7 at /usr/sbin/luksformat line 63, <MOUNTS> line 15". If you get the error message "Device luksformat1 is busy" after the format has completed, execute "cryptsetup luksClose /dev/mapper/luksformat1". We now mount the newly created encrypted partition and copy our Backtrack installation to to. For this execute the following commands:
- cryptsetup luksOpen /dev/sda7 cryptoroot
- mkdir /mnt/target
- mount /dev/mapper/cryptoroot /mnt/target
- cp -avx / /mnt/target
Copying can take a while. Once completed open /mnt/target/etc/fstab and find the section that refers to the partition where the unencrypted Backtrack system was installed. It can be recognized by the line above it which contains "# / was on /dev/sdaX during installation". The line under it will look something like this:
UUID=00adfd86-26d7-445c-8d4a-e72b16400423 / ext3 errors=remount-ro 0 1
We need to change the UUID of it to the UUID of the encrypted partition. To get the UUID execute "blkid | grep /dev/mapper/cryptoroot". Once you know the UUID update the line with the new UUID.
Testing with GRUB
Before we continue we will add a temporarily entry to GRUB to verify we can boot the encrypted Backtrack system. To do this edit /boot/grub/menu.lst and under the line "### END DEBIAN AUTOMAGIC KERNELS LIST" add the following lines:
title Cryptotest
root (hd0,4)
kernel /vmlinuz-2.6.38 root=UUID=<uuid> ro
initrd /initrd.img-2.6.38
boot
Here (hd0,4) stands for the boot partition. You can get the correct kernel version by looking at the lines between the DEBIAN AUTOMAGIC KERNELS entries. Replace
<uuid> with the UUID of the encrypted partitions, which can be found by executing "blkid | grep /dev/mapper/cryptoroot".
Reboot the system and press ESC to enter the GRUB menu during boot. Select cryptotest from the menu. If something goes wrong restart and choose Ubuntu in the grub menu and try to figure out what when wrong. If you followed this guide everything should work.
Encrypted Swap
This step is best performed from the Cryptotest environment we just added to the grub boot menu. You can also perform it from the unencrypted Backtrack installation but then you must be sure to mount the encrypted partition and modify the correct files. This guide will assume you are running the Cryptotest option (i.e., the encrypted Backtrack system). The following procedure will make sure that the swap will also be encrypted.
This is important because sensitive data can be written to the swap when using your computer.
We will first disable swap and destroy the filesystem on the swap partition. For this execute the following two commands:
- swapoff -v /dev/sda6
- dd if=/dev/urandom of=/dev/sda6 count=100
Open /etc/crypttab and append the following line to the file:
cryptoswap /dev/sda6 /dev/urandom swap
Now open /etc/fstab and replace the line under "swap was on /dev/sda6 during installation" with:
/dev/mapper/cryptoswap none swap sw 0 0
To test if everything is set up properly execute the following commands:
- invoke-rc.d cryptdisks restart
- swapon /dev/mapper/cryptoswap
Now the command "swapon -s" will show you the loaded swap partitions. It should contain the cryptoswap entry if everything is configured properly.
Final GRUB Config
Time to configure a proper GRUB menu. Open /boot/grub/menu.lst and remove the "Cryptotest" lines that you added earlier. Search for the line containing "# kopt=root=UUID=<uuid> ro" and replace the UUID with the UUID of /dev/mapper/cryptoroot. Remember that you can get this UUID by executing "blkid | grep /dev/mapper/cryptoroot". Once this is done execute the command "update-grub".
In my case the default splash screen prevented you from correctly entering the password during boot. For this reason we will remove the splash screen during boot. Open /boot/grub/menu.lst and remove the "quiet splash" from the first line in the entry for "Ubuntu 10.04 LTS, kernel 2.6.38". If you want to you can change the title to display Backtrack 5 instead of Ubuntu. As suggested by a commenter, you must also to change "defoptions=quiet splash" to "defoptions=". This will make sure running update-grub will not readd the "quiet splash" argument in the future. Optionally, if you want the grub boot menu to be displayed by default during boot, you can comment out "hiddenmenu" by changing it to "# hiddenmenu".
Note: To finish the complete setup of Backtrack execute "apt-get update" and "apt-get upgrade" in order to update all the packages.
Installing Windows
Before we can install Windows we must create a NTFS partition where it can be installed. To do this boot your Backtrack installation (or do this from a live CD) and install gparted by exeucting "apt-get install gparted" and run it by executing "gparated".
Right click on /dev/sda1 which was the partition where you installed the unencrypted Backtrack installation. Select Format to -> NTFS. Then go to Edit -> Apply All operations to save changes to disk. If for some reason these steps didn't work for the first time and /dev/sda1 still showed up with a file system other than NTFS, simply format /dev/sda1 a second time and it should work.
You can now enter the Windows installation CD and reboot. Continue the windows installer as normal until you get to "Which type of installation do you want?". Here select "Custom (advanced)". In the next screen select "Disk 0 Partition 1 and click" on next.
Once Windows has been installed download and install
Truecrypt.
Start Truecrypt, click on System ->Encrypt System Partition/Drive. Choose normal, Encrypt the Windows system partition, Single boot, select your preferred encryption options (the defaults should be good), and continue with the installer while providing the information it needs. Be sure to create the rescue CD as this is very important in case the truecrypt bootloader gets damaged. If it asks you to restart the system do so. During boot you should see the Truecrypt boot loader (we will soon restore the GRUB boot loader). It will ask you for the password, enter it and continue booting.
When Windows is started it should ask to encrypt the Windows partition. Click on Encrypt. This can take a while depending on the size and speed of your hard disk. Go get a beer, watch a movie, and take a break.
Once it's done you can verify everything still works by rebooting Windows.
Restoring GRUB
Boot from the Backtrack live CD. We will first copy the truecrypt bootloader as a file to the linux boot partition. To do this open a terminal and do:
- Mount the boot partition be executing "mount /dev/sda5 /mnt"
- Copy the truecrypt boot loader by executing the following two command
- dd if=/dev/sda of=/mnt/truecrypt.mbr count=1 bs=512
- dd if=/dev/sda of=/mnt/truecrypt.backup count=8 bs=32256
We will now restore the grub boot menu by executing the commands:
- apt-get install grub
- grub
- Execute "find /grub/stage1". This should output the line "(hdX,Y)" where X and Y are numbers depending on how you set up your partitions. These numbers will be used in the next commands. In my case the output is "(hd0,4)".
- root (hdX,Y)
- setup (hdX)
- quit
Now let's add the truecrypt boot loader as an option to the grub loader. Open /mnt/grub/menu.lst in your favourite editor. Under the line "### END DEBIAN AUTOMAGIC KERNELS LIST" add the following lines:
title Windows 7
rootnoverify (hd0,0)
makeactive
chainloader (hd0,4)/truecrypt.mbr
boot
And there you go. You have a fully encrypted Windows partition with a dual boot between a fully encrypted Backtrack 5 installation.
Sources
Inspiration was taken from the following sources, a few man pages, and relied on some creativity to solve problems along the way.
Encrypted Ubuntu Partition
Reverting to GRUB Legacy
Restoring GRUB
Bug: Unable to enter password
Chainloading Truecrypt